Bybit hacker swaps $3.64M to DAI via decentralized exchanges
Addresses associated with the Bybit hacker have been spotted using decentralized exchanges (DEXs) to trade cryptocurrencies for Dai, a stablecoin that lacks a freeze function.
Recent blockchain records reveal that a wallet receiving some of the Ether (ETH) stolen in the $1.4 billion Bybit hack on Feb. 21 has interacted with platforms including Sky (formerly MakerDAO), Uniswap and OKX DEX.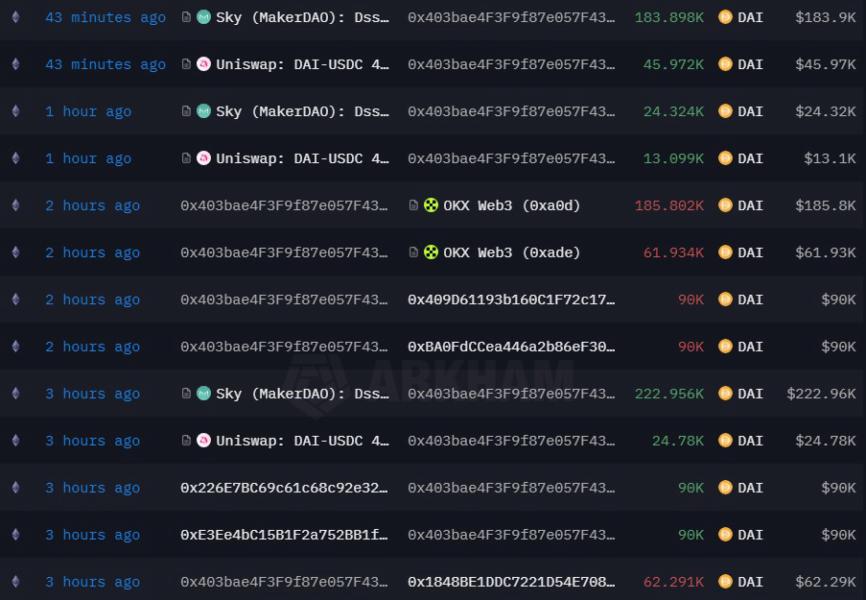
According to copy trading platform LMK, the Bybit exploiter sent $3.64 million worth of ETH to one address, which was then used to swap ETH for Dai (DAI).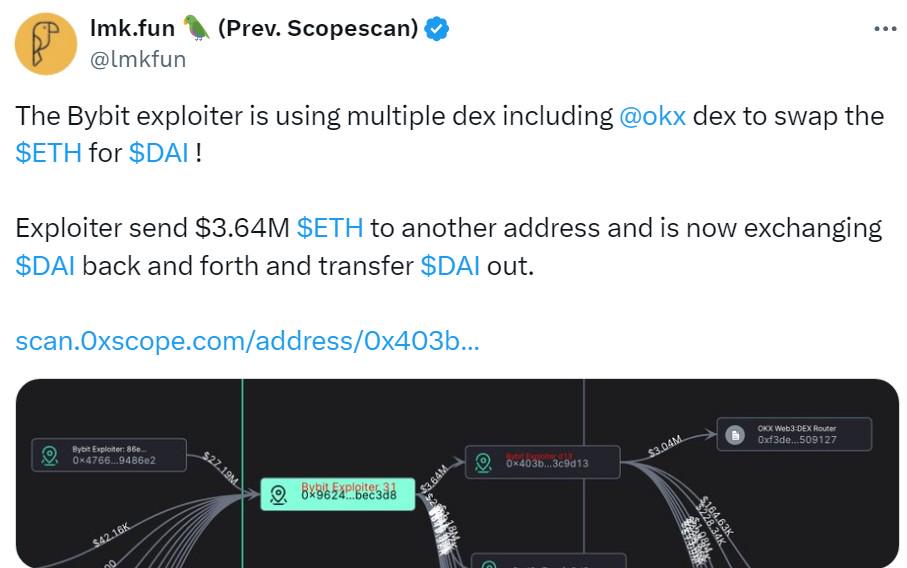
Unlike centralized stablecoins such as USDt (USDT) and USD Coin (USDC), managed by Tether and Circle respectively, DAI cannot be frozen by a centralized issuer, making it a valuable asset for cybercriminals.
EXch refuses to freeze Bybit hack proceeds
The Bybit exploiter appears to be splitting the DAI holdings into multiple addresses. Some funds have been directly deposited into non-Know Your Customer cryptocurrency exchange eXch, while some have been swapped back to ETH.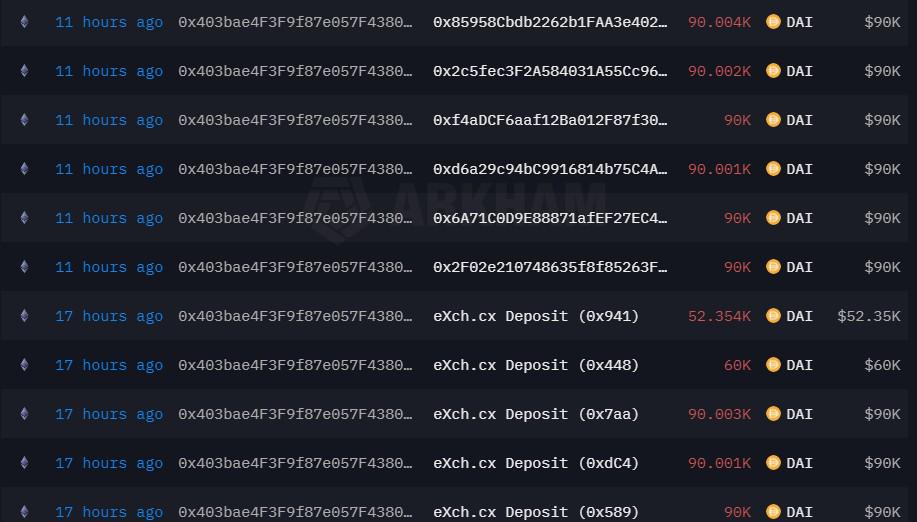
EXch has been the center of controversy since the Bybit hack, as it refuses to freeze funds related to the exploit. In contrast, other exchanges and protocols have provided assistance to Bybit, including freezing addresses involved in the hack and offering loans to cover losses.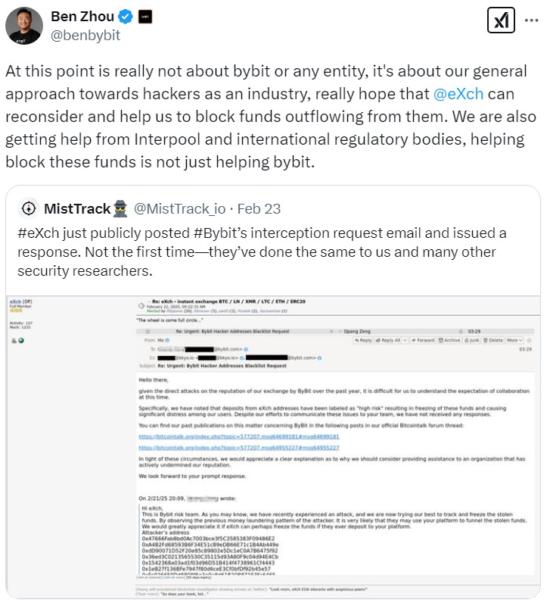
“Given the direct attacks on the reputation of our exchange by Bybit over the past year, it is difficult for us to understand the expectation of collaboration at this time,” eXch stated in an email to Bybit, which was later posted on the Bitcointalk forum.
Tether CEO Paolo Ardoino announced on Feb. 22 that the company had frozen $181,000 in USDT associated with the Bybit hack. But some tokens slip through. Cointelegraph has learned of a transaction linked to the Bybit hack that resulted in 30,000 USDC reaching eXch.
Lazarus link to Bybit hack deepens
Onchain investigator ZachXBT has identified North Korean state-sponsored hacking group Lazarus as the prime suspect in the Bybit hack. The investigator identified a common address used by the Bybit hacker in previous attacks on Phemex and BingX, both attributed to Lazarus.
Most recently, ZachXBT noted that these three exploits also share an address with the Poloniex attack.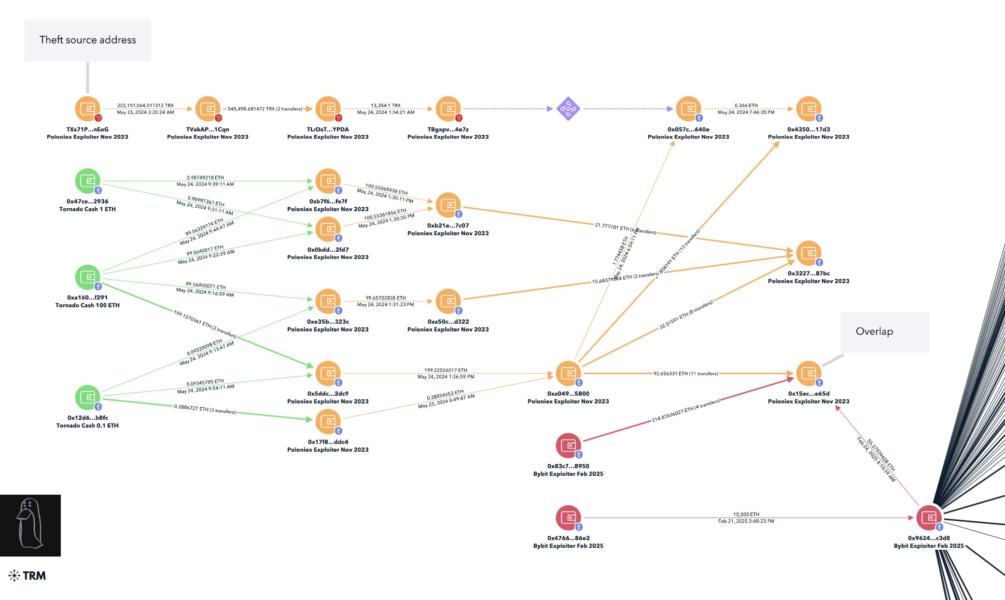
EXch has denied claims by industry observers that it has been laundering money for Lazarus or North Korea.